Restricted groups certainly aren't anything new, they've been available with Windows Server GPO's for several versions now. They allow you within a domain GPO to specify the membership of a specific group on the target machines, therefore saving you the hassle of doing it manually.
In this instance the aim was to grant local administrator permissions to a selection of users, but only to the client machines on the network, not the servers. Eg, those users could make changes, install software etc on the desktops and laptops within the companies network, but could not login to the servers, and therefore gain access to data they were not authorised to view.
A reasonable guide can be found here, however, the critical ommission is that the "Group Name" MUST be the name of the group that you want the users / groups to be a member of on the client machines. The instructions indicate that it's controlled by "Member Of", however from testing that appears not to the the case.
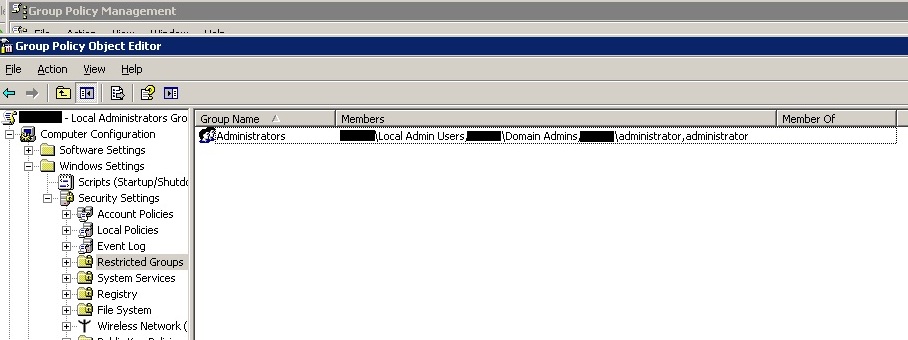
So to add MyAdminGroup to the Administrators group you would set :
Group Name = Administrators
Members = MyAdminGroup, Administrator,
Member of = empty
All the guides I've seen show the group name in their examples as being "Administrators", but make no reference to this being anything other than a simple name. When I first attempted it, I called the group "Local Admins", and then added "Administrators" (and a few other variations) to the Member of section, with no effect.
Note: When using Restricted groups you need to include the existing groups as well as the new ones, as this policy replaces rather than amends the existing group membership.
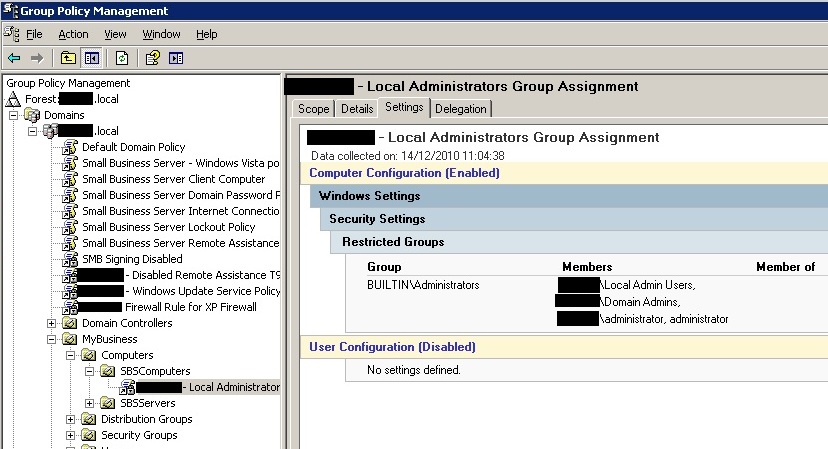
You can see screenshots of how this looks below :
Group Policy Manager
Group Policy Editor